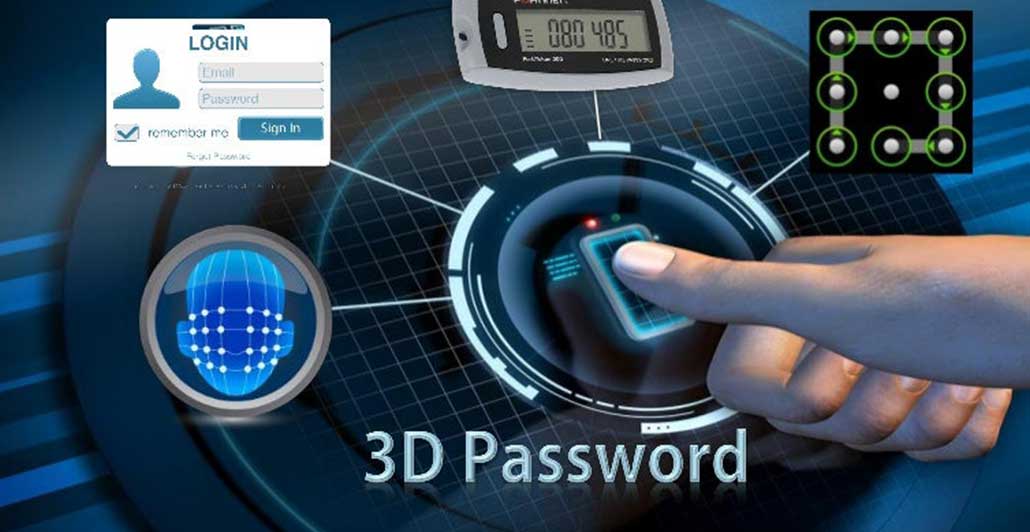
A Complete Guide about 3D Password
Quick Summary: A 3D password adds a variety of authentication techniques into a single 3D space improving security. Instead, users move through a virtual environment, manipulating objects that result in the generation of difficult to forge passwords. This method provides high security and flexibility, securing data that is not to be exposed to third parties. Let’s read more what this methods provides!
Definition of 3D password
Users nowadays are provided with the major password stereotypes such as textual passwords, biometric scanning, tokens or cards (such as an ATM), etc in 3D Password.
Mostly textual passwords follow the encryption algorithm mentioned above. Biometric scanning is your “the natural” signature and Cards or Tokens prove our validity.
But a number of the people hate the actual fact that they carry around their cards, some refuse to undergo strong IR exposure to the retinas(Biometric scanning).
Mostly textual passwords nowadays are kept very simple, say a word from a dictionary or their pet names, girlfriends, etc.
The Year back Klein performed such tests and he could crack 10-15 passwords on a daily basis.
Now with the technology change, the fast processors, and lots of tools on the net, this has become a Child’s Play.
Introduction of 3D password
Therefore we present the thought, the 3D passwords which are quite customizable and an awfully interesting way of authentication.
Now passwords are a supported fact of Human memory.
The human memory, in the scheme, must undergo the facts of the popularity, Recalling, Biometrics, or Token supported authentication.
Once implemented and you log in to the secure site, the 3D password GUI releases.
This can be an extra-textual password that the user can simply put. Once he goes through the primary authentication, the 3D virtual room will open on the screen.
In our case, let’s say a virtual garage.
Existing System
- Textual the password
- Graphical the password
- Biometrics
- Token-based

How secure is your password?
Now with the technology change, the fast processors, and lots of tools on the net, cracking passwords has become a child’s play.
Years back Klein performed such tests and he could crack 10-15 passwords on a daily basis.
The 3D password is more customizable and it’s an awfully interesting way of authentication.

A 3D password may be a multifactor authentication scheme that mixes RECOGNITION+RECALL+TOKENS+BIOMETRICS in one of the authentication systems.
The 3D password presents the virtual environment containing various virtual objects.
The user walks through an environment and interacts with the objects.
It is the mix and sequence of the user interaction that happens within the 3D environment.
Brief description of the system
The user is presented with this 3D password in the virtual environment where the user navigates and interacts with various objects.
System Implementation
For example, a user can enter the virtual environment and also enter type something on a computer that exists in the (x1, y1, z1 ) position, then enter an area that incorporates a fingerprint recognition device that exists during a position (x2, y2, z2 ) and supply his/her fingerprint.
Then, the user can visit the virtual garage, open the door, and switch on the radio to a particular channel.
The mixture and therefore the sequence of the previous actions toward the precise objects construct the user’s 3D password.
Virtual Object
- A virtual object may be any object we encounter in real life.
- A paper or the whiteboard that a user can write, sign, or draw on.
- An automatic teller machine (ATM) that requests a token.
- A lightweight which will be switched on/off.
- A television or radio where channels will be selected.
- A computer with which a user can type.
- A fingerprint reader that needs the user’s fingerprint.
- A biometric recognition device.
- A staple that may be punched;9) A car that may be driven.
- A book that will be moved from one place to another.
- Any graphical password scheme.
- Any reality object.
- An upcoming authentication scheme.
Conclusion
In conclusion, the use of a 3D password system is a unique and more secure approach towards authentication by integrating many practices into one environment. This innovative technology broadens security against unauthorized access through the technique of personalized 3D spaces that will be hard to mimic passwords. Thus, the application of the 3D password does not become hindered when the cyber threats are changing, and it remains a flexible and quite functional way of solving the problem by keeping the balance between security and convenience. Adopting this will enhance approach in authenticating users can go a long way in enhancing security of digital assets. And makes it a viable option, especially for parties that are in need of enhanced security of their data.
FAQ
What is a 3D Password?
A 3D Password uses a 3D virtual space for identification, and it is a modern approach to the concepts of security and protection. It involves a user’s ability to change an object within a particular space, normally in an online forum, into a password. In this case, the letters constitute of interactions including movement, selection or manipulation of objects make it hard for the intruder to mimic the 3D Password.
How does a 3D Password differ from traditional passwords?
While normal passwords incorporate strings of characters or even a PIN number, 3D Passwords are different in that they incorporate an animated environment where the password is created based on the actions the user performs. This increases the sophistication and security aspects by adding layers of dimensions and can include quite complex pattern and movements like click, drag and manipulate and only supports text only which proves to be comparatively less secure.
What are the security advantages of using a 3D Password?
The primary security feature 3D Passwords is immune to common attacks with brute force, dictionary attacks, and shoulder surreptitious observation.
Are there any challenges or limitations associated with 3D Passwords?
Although there exist some benefits of using 3D Passwords, there are also some drawbacks too. These are: the need to have special software and hardware to develop as well as to navigate within the 3D space, which may be a hurdle to those without the equipments. Furthermore, the learning of the system and time needed to implement the first-time password might also be higher than with password use and can pose difficulties for users who are not conversant with virtual environments.
In what scenarios are 3D Passwords most beneficial?
In this reason, 3D Passwords are mostly useful in a security-sensitive organization where conventional types of authentication do not adequately protect. They are most suitable for use in bodies which handle sensitive data such as the banking sector, the military, the government and in research institutions. Also worth noting, 3D passwords can become effective when used to safeguard information on the devices applicable to 3D solutions, thus enhancing security for users who may need it beyond basic safely features.